I will see what the status is, thanks.
We will support it when Microsoft adds support for the Linux Subsystem with their own Firewall API. Currently we can’t do so from what I understand.
Any idea when MS will add support for the Linux Subsystem to their Firewall API?
At least the Linux Subsystem itself will be out of beta soon …
Have to say that’s not a great answer.
Only Glasswire has a problem and only when “Ask To Connect” is selected, in all other modes the linux subsytem works fine (i.e it’s fine with “Click to block” - but of course that defeats the purpose of installing Glasswire).
Can you not at least add the option of an exemption from “Ask To Connect” for the subsystem? I’d be fine running the security risk that the subsystem bypasses Glasswire
We’d love to make it work of course but from what I understand it’s not technically possible.
Are you saying if you block the Linux Subsystem with our “Click to block” it blocks it successfully?
As @kk2 says in the very first message in this thread (paraphrasing):
If “Ask to connect” is enabled, then the linux subsystem cannot connect to the internet at all
If “Click to block” is chosen, or the firewall is turned off, then the linux subsystem can connect to the internet
This is related to the “pico” process that windows uses to implement the linux subsystem - MS treat this process/subsystem differently (as mentioned in links provided above).
In lieu of a proper solution, I suggested you have an option that can be selected to exempt “pico” from the “Ask to connect” filtering (i.e optionally a blanket rule that always allows pico to connect), this is sub-optimal but would allow those of us with the problem to continue using Glasswire in its “Ask To Connect” mode (the reason after all I paid for Glasswire).
This was first raised in August last year, now we appear to have gone full circle and recent questions were answered earlier. Sadly I’ve exhausted my enthusiasm to help further, this thread has everything your team should need to reproduce and understand the problem, no-one expects an overnight solution.
I’ll put paying for a licence down as a mistake and move on to an alternative product. It’s a shame, Glasswire is pretty but doesn’t work properly.
GlassWire works properly, but it has some issues offering support for a beta Microsoft software that Microsoft isn’t yet supporting with their own Firewall API.
However, that’s a really great idea having the checkbox. I will ask if it’s possible to implement this idea but I’m afraid they are going to say that since the Firewall API can’t properly deal with “Pico” that even this check box won’t work. I hope I’m wrong though!
I understand your frustration and I apologize for the problem. We really do care about this and we are equally frustrated.
Some news…
We did some more research and it appears Microsoft will probably support this before the final release.
They asked that you all report the problem here https://wpdev.uservoice.com/forums/266908-command-prompt-console-bash-on-ubuntu-on-windo/ so it will be more likely to be fixed faster.
Please vote here: https://wpdev.uservoice.com/forums/266908-command-prompt-console-bash-on-ubuntu-on-windo/suggestions/18918169-windows-firewall-should-support-pico-wsl
Meanwhile our team had some options for you @rob and others.
-
Open Control Panel\System and Security\Windows Firewall;
-
Run Advanced Firewall settings on the left panel;
-
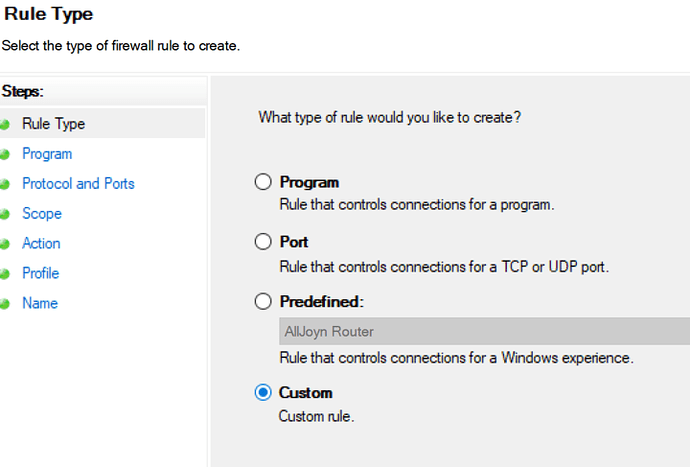
Add an outbound rule and select a custom rule, then click Next;
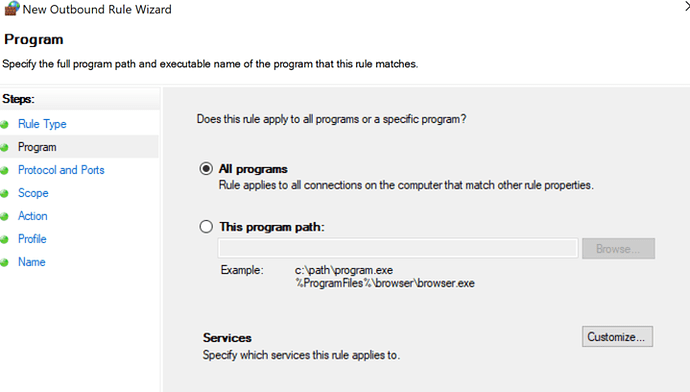
- Select All programs and click next;
-
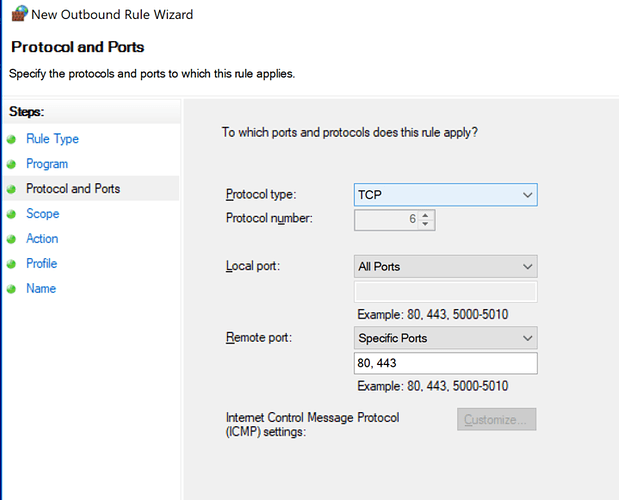
Select protocol type and specify the remote ports and click next;
-
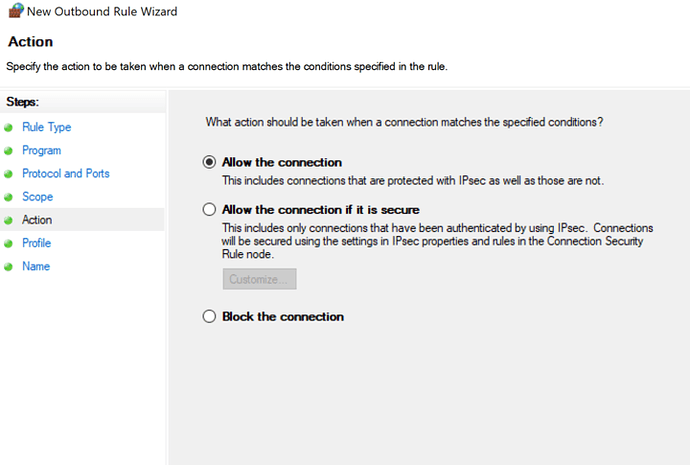
Select Allow the connection, specify the rule name and apply it.
This will add an exception for connections to a specific port or port ranges. So if you know exactly which ports are required for the linux app, you can make an exception.
I hope this helps until the Microsoft team fix is implemented.
Thanks - I have voted on the link suggested. Blanket opening of ports isn’t really a viable option (especially the 80, 8080, 443’s of this world), but thank you for the suggestion.
Any news on this matter? 1709 is out, WSL not beta anymore
Well, it has been announced a good while ago that WSL would be out of beta with the release of the Fall Creators Update, see for example here:
https://blogs.msdn.microsoft.com/commandline/2017/07/28/windows-subsystem-for-linux-out-of-beta/
Now with the Fall Creators Update officially released, see another announcement here:
Sure, I just wanted some confirmation that the Linux subsystem is out of beta so I can ask our team to hurry up and support it. Currently I am having trouble finding any confirmations anywhere. I agree we should support it ASAP but I wanted to be sure it’s really the final version before we spend major time working on something that could get a big change before the final version.
I see now in the link you sent that the Windows subsystem is actually out of beta. I’ll alert the team and see what can be done. Thank you all for your patience.
We just checked and it appears there is still no Windows Firewall support. GlassWire uses the Windows Firewall API. We cannot do anything until they close out this bug https://github.com/Microsoft/BashOnWindows/issues/722 but perhaps you can let Microsoft know this fix is important for you and we will do the same.
Ok, I see. I have seen that some API was ready for a good while, but indeed the firewall team at MS didn’t incorporate that as yet - bad.
Somebody tried something with a proxy on the Windows side to pass the WSL traffic through, maybe that would be a workaround. I will try that out when I find the time (which might be never … lol)
Anyone running into this problem, please upvote this on Windows UserVoice:
A “solution” I’ve been using is to:
- install a socks5 proxy (e.g dante) on another machine (assuming you have one)
- Configure a hole in Windows Firewall from your machine to the proxy for the specific port you set it up on
- Disable glasswire
- Install “proxychains” with apt get
- Re-enable glasswire
- Configure proxychains to use the socks5 proxy
- Run processes that require network access using proxychains (e.g: sudo proxychains apt get update)
Klunky as hell, won’t work for everything and not really long term viable, but may get you somewhere.
It does appear everyone is waiting on Windows to pull their stuff together and come up with a suitable solution
I also go through a proxy, albeit on the same machine (works for me). Thanks for mentioning proxychains, haven’t used that as yet, seems easier than configuring a ton of things to use the proxy.
There is a discussion at Microsoft about Windows Firewall and WSL, and it seems like they are now working on that. Not for the next update in spring, but maybe for the one after before the end of the year - let’s keep our fingers crossed.
As was posted today:
“Better Windows firewall support [for WSL] is now live in the Skip-ahead 17627 build.”
As it is in Skip-ahead, it means that it won’t be in the next Windows update due in in spring, but in the one after. Maybe the Glasswire engineers can have a look to figure out if that is what they need.