I am running Windows 10. What virus scanning engine is does GlassWire use? It cant be my installed Emsisoft AntiMalware because there is no scan log recorded and GlassWire still scans even if Emsisoft is disabled. Windows defender is also permanently disabled.
We use a Windows API for the scanning and I think it’s the built in Windows antivirus that scans.
There’s several questions about GlassWire virus scanning that haven’t been answered definitively so I thought I’d have a look at this one.
I don’t have Emsisoft AntiMalware (EAM) to test the situation for @kpat50. I assume that EAM does perform the scan but leaves no log accessible from the EAM user interface. I say this because that has been the case with every antivirus product that I have used with GlassWire including Avast, Avira, and 360TS.
Anyway, there seems to be two easy tests to find out if Windows Defender is the default even if it is disabled:
- Try to do a manual scan when Windows Defender is disabled.
- Try to do a GlassWire virus scan when there is no antivirus installed and Windows Defender is disabled.
If there is no definite answer then a more difficult test is to 3. trace which process is performing the virus scan - I’m not sure if I’ll do that.
1. Try to do a manual scan when Windows Defender is disabled
On Windows 10 with Windows Defender disabled, I tried to initiate a manual file/folder scan with Windows Defender.
The manual scan doesn’t work with Defender as I got the following error message:
CmdTool: Failed with hr = 0x80004005. Check C:\Users\Me\AppData\Local\Temp\MpCmdRun.log for more information
0x80004005 is the same error code that I would get if my antivirus software wasn’t running properly when called by the Windows API, e.g. as with https://support.microsoft.com/en-us/kb/329936
The log file entry shows that Defender remains disabled even for a manual scan - I’ve added the bold emphasis:
MpCmdRun: Command Line: “C:\Program Files\Windows Defender\mpcmdrun.exe” -scan -scantype 3 -file c:\users\me\text.txt
Start Time: Sat Aug 13 2016 19:34:27
Starting RunCommandScan.
WARN: Product/Feature disabled
MpCmdRun: End Time: Sat Aug 13 2016 19:34:27
My tentative conclusion is that disabling Windows Defender prevents it being used for GlassWire scans. I’ll run test 2 to confirm this when I get some free time.
2. Try to do a GlassWire virus scan when there is no antivirus installed and Windows Defender is disabled
I uninstalled my antivirus with Defender disabled. Windows 10 notified me that there was no virus protection:
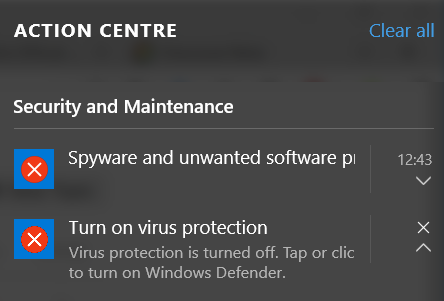
I used GlassWire to confirm that the antivirus program was not installed. When I tried to scan the executable the result is “Unscanned” because the executable cannot be found:
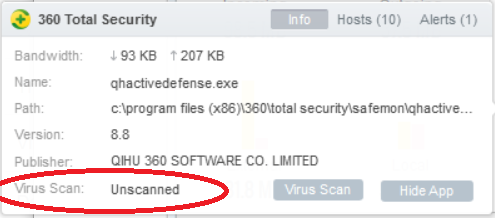
However, I could still scan even with no antivirus installed/enabled. This was also the result when I tried it last year:
-
GlassWire continues to show Virus Scan results:
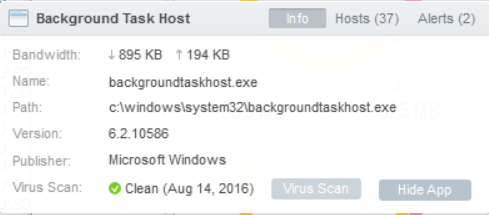
-
GlassWire continues to show a notification.
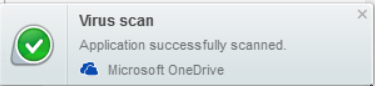
My tentative conclusion after the tests 1 and 2 is that GlassWire is not using either Windows Defender or my installed antivirus because scans continue even when I have no active antivirus protection.
After reinstalling my antivirus, I realized that I should have run test 1 again to confirm that Defender is definitely not enabled.
As an aside, @Ken_GlassWire, why don’t I have any control over the virus scan notifications in GlassWire settings?
- I don’t want a notification when I have initiated the virus scan so I want an option to turn this off.
- The virus scan notifications don’t appear in the alert list. However, it would be useful to know if someone else has initiated a virus scan on a remote computer.
Although the Windows Defender user interfaces are not being used, it seems most likely that the Windows Defender API is. The GlassWire virus scan completes even if there is no network connection so the scan must use a local database.
So is GlassWire calling the IOfficeAntiVirus Module - MpOav.dll and using the Defender database?
There appear to be two Defender databases that are used. See “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Signature Updates” for the locations.
I checked that neither are up to date on my system:
- AV/malware updated January 2016
- Network Inspection System (NIS) updated October 2015
What is bothering me about the GlassWire virus scan is that if the databases are not up-to-date then we may have misplaced our confidence in the value of a GlassWire virus scan.
An aside related to the topic of third-party scanning is that the Windows 10 Anniversary Update provides a new feature, Limited Periodic Scanning, to allow Windows Defender real-time protection to be turned off but have automatic periodic/batch scanning enabled.
This feature is aimed at home users who have a third-party antivirus program installed. Apparently, this feature is not available for “managed devices”, i.e. those administered using Group Policy such as on corporate networks. So it appears that this feature is not limited to specific Windows editions.
At present, it is possible to do something similar using the Microsoft Safety Scanner. The problem is that the Microsoft Safety Scanner expires 10 days after downloading so it must be downloaded ad infinitum.