What router do you have?
@Tarun
I use Cloud Flare as a CDN and now I want to uninstall. I see many video but still the CDN is not properly delete what should I do?
@davidoyama this FAQ will help you in removing the CloudFlare CDN from your website/domain.
Okay fine, let me know what should I do, how I change my DNS to my original hosting.
@davidoyama I did, check the link to the FAQ.
If you’re not referencing a website, then simply remove the CloudFlare DNS from your router or computer. Typically, just deleting the DNS entries to being blank will reset them to the ISP provided DNS.
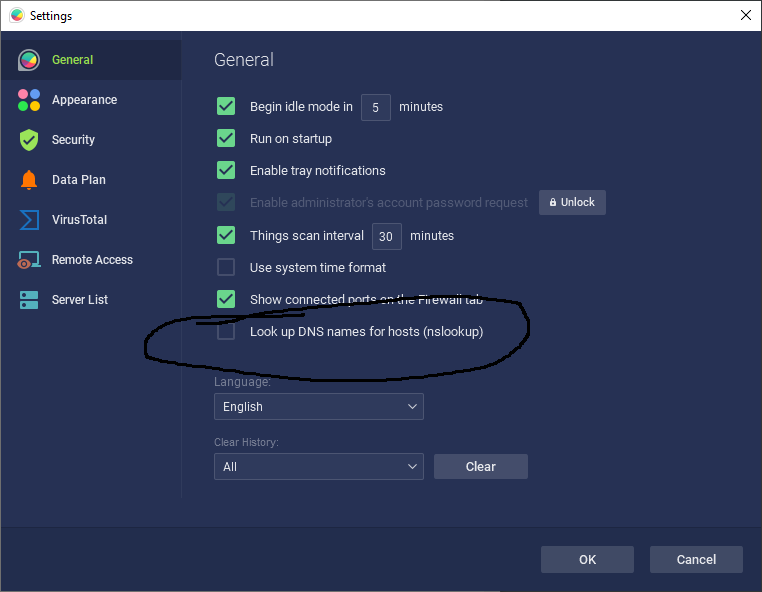
Our next update will allow you to have the ability to turn off nslookups. Here is a sneak preview below!
FYI - Up to date, concise and technical:
Primary focus is on enterprise admin but here’s a pull quote for the average home & mobile user:
If you are an end-user, with your own personal (non-employer-owned) machine, your main concerns should be about whether any alternative DNS resolver (beyond manually configured or DHCP provided) is enabled/configured. The main issue with this would be when you are using someone else’s network and whether you are violating their policies or expectations. This is particularly true when traveling to other countries when this small change might violate local laws. This may also be true in a BYOD (bring your own device) environment, where this could violate your employer’s policy, with potential employment-related consequences.
GOOGLE CHROME UPDATED INFO
As of v78, the executable run command line cited in the article is replaced by an internal flag:
chrome://flags/#dns-over-https
Cheers.
In Firefox, if you turn on DoH via the GUI it should handle it in the config automatically. No need to go to about:config.
For what it’s worth, keep in mind that GoDaddy is also against a free and open Internet. SOPA, etc, they backed.
I mention this because:
A version of this post was originally published in the GoDaddy Engineering blog.
By Brian Dickson, Principal Software Development Engineer at GoDaddy
Our update that allows you to turn off nslookups will be out next week.
GlassWire can now disable nslookups.
Version 2.1.166 - (September 17, 2019)
Hash # 2E394CA96D8AE6075879891365857A8FFF5E8AE14162DEA25CA39410C90F473D
Turn nslookup off in your GlassWire settings if you don’t want to see the domain names of the hosts you are connecting to.
Changes were made on how the Windows “System” and Windows Defender are handled with the firewall.
Graph screen optimizations to use even less resources when using GlassWire.
New help screens to help with technical issues.
Other bug fixes and enhancements.
Hi Ken,
I always look forward to new versions and the changes. Myself and others might be interested to know what were the…
" Other bug fixes and enhancements".
Just a thought, and curious to know … Thank you Ken, and the Glasswire team.
Sometimes people report little UI bugs and things. It’s nothing significant so that’s why we don’t mention it. If I listed them all it would just look ugly on the change list and be too much to read.
https://www.glasswire.com/changes/
It will handle it but one must go to about:config to disable the default (aka native) system fallback by setting the necessary values in network.trr.bootstrapAddress and network.trr.mode.
The values I’ve used for over 6 months without issue are shown in my post 12 above. The bootstrap address 1.1.1.1 is valid for either cloudflare-dns.com/dns-query or mozilla.cloudflare-dns.com/dns-query in network.trr.uri.
@ Ken_Glasswire
I updated to 2.1.166 from 158. and I take it that the hostname_enable_nslookup in the conf file is no longer needed. I had mine set as true.
The file as shown in my post 5 above now reads as:
db_file_path=C:\ProgramData\Glasswire\service\glasswire.db
geoip_db_path=C:\ProgramData\Glasswire\service\GeoLite2.mmdb
storage_path=C:\ProgramData\Glasswire\service\storage.db
hostname_storage_time=21600
enable_database_check=false
As shown in your screen shots and on my system, the option is not checked. So the default is Off?
Thanks!
That defeats the purpose of the fallback. A fallback is by design made so that if something fails, it goes to something else that will still work.
Jeez, Tarun, a truly a brilliant forensic analysis. Who knew?! And a “something else that will still work”? No failures ever… Hallelujah.
There was never a fallback for DNS ever. Or HTTP or HTTPS for that matter. (Set ON for “encrypt all sites eligible” in HTTPS Everywhere and watch which sites are still on HTTP and are blocked from loading, thankfully not many these days.)
The current fallback, in reality a temporary fail-safe, in Firefox is analogous to testing a hardened entrance (steel door and frame, Class 1 locks, etc.) and next to it is the regular door with the plain old no-lock door knob which has been used ever since the file room was built.
Firefox will eventually remove the fallback globally once the selective DoH roll-out is deemed a success now that the “experiment” has concluded. As one of the 70,000+ people involved, it was a whole lotta fun.
“We’ve also been surprised and excited by the more than 70,000 users who have already chosen on their own to explicitly enable DoH in Firefox Release edition.” - Selena Deckelmann, Mozilla Blog
Anyhow, it looks like my post 33 will remain unanswered and I’ve grown weary of this ineffectual discussion. I won’t be revisiting this thread.
My original request for DNS security/privacy in GlassWire remains. It will ultimately determine my continued use of one of my favorite apps. As of now, I’m disabling this really, really useful feature.
Cheers.
Can you show , how ?
Sorry for the late answer, I missed this somehow. The default is that we do DNS lookups. You must disable the feature.
DNS over HTTPS (DoH) is a protocol for performing remote Domain Name System (DNS) resolution via the HTTPS protocol. A goal of the method is to increase user privacy and security by preventing eavesdropping and manipulation of DNS data by man-in-the-middle by using the HTTPS protocol to encrypt the data between the DoH client and the DoH-based DNS resolver. Encryption by itself does not protect privacy, encryption is simply a method to obfuscate the data. As of March 2018, Google and the Mozilla Foundation started testing versions of DNS over HTTPS.
In case someone in the future comes across this thread, there is another strong reason to use DoT over DoH.
DoH contains metadata such as user-agent. This may also include system information and is sent to the DNS server.
DoT does not send this kind of information.
A user-agent can say a lot about you and your system: https://www.whatsmyua.info/