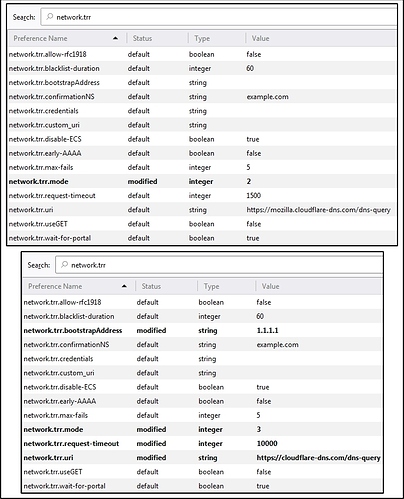
I’ve been using Firefox’s DNS-over-HTTPS (DoH) for almost a year. Search firefox doh in an engine of your choice.
It’s been so reliable, months ago I enabled mode 3 and bootstrapped the IP address to disable fallback to system DNS.
In this quick & dirty screen shot while opening a popular news aggravator, 1.1.1.1 (Cloudflare) is opened upon first connection out and persists throughout the session for secure NS lookups. Secure insofar as trust in Cloudflare and Mozilla is concerned. Other DoH servers exist and can be used by Firefox.
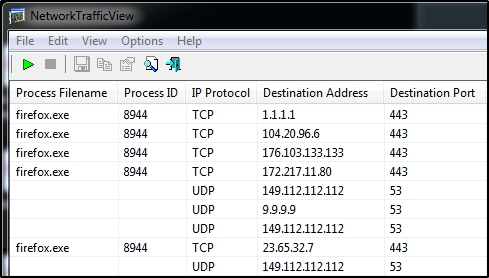
Note the port 53 connections to 9.9.9.9 and 148.112.112.112, my system TCP settings for Quad9. (These, of course, would be different for everyone else using other DNS servers or ones configured via ISP DHCP or router settings.)
GW does these port 53 lookups thereby upsetting DoH’s core mission of NS lookup privacy while browsing teh webbuhnetz. These lookups do not compromise DoH’s browser protection against the legion of DNS exploits.
Consequently, disabling GW’s NS lookup would upset the display and logging of valuable network detail.
Given the infancy of secure DNS, overdue by 20 or so years, there is no faulting GW or any other utility in this regard. As well, everything else on the system (RSS, email clients, et al) does the insecure port 53 boogie.
But in looking ahead, GW might consider implementing user configured DoH functionality, optionally. Easier said than done, of course. I wonder if the folks over at The Qt Project have it under consideration, waiting on Linux and Windows to write it into their kernels where application enabled DoH would no longer be essential.
IMHO, DoH will win out over DoT (DNS over TLS).