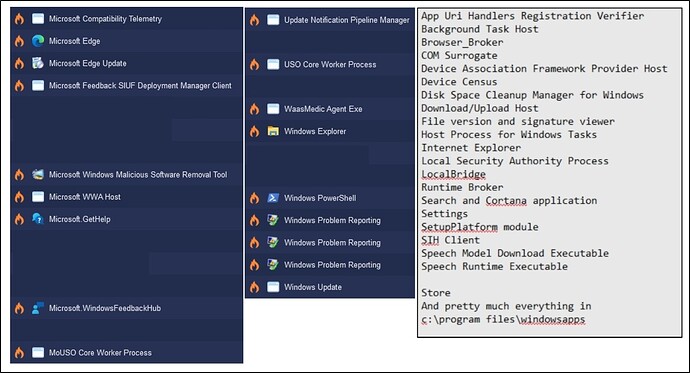
I find Glasswire very difficult to understand and use. When I go to settings/privacy etc. on my windows 10 piece of junk there is NO OPTION to stop sending activity to Microsoft as all the articles say there is. There are only options to clear history ie. my email.
So can I use Glasswire to disable my box from sending ANY AND ALL info to MS? Like if some app crashes I immediately get a message that that info is going To MS etc.
Along these lines I have disabled those invasive endless updates long ago but that played havoc with the machine so now I had to reenable them.
All the garbage Microsoft forces you to eat is ultimately installed to spy on you for whatever reasons and I’m sick of it.
For now though, can someone say exactly and simply, like talking to a moronic 3 year old , the precise way to get Glasswire to disallow any outgoing stuff to of any type to that giant evil corporation?
Thanks